Search This Blog
Saturday, December 11, 2010
How to Sharpen a Knife or Chopper
Introduction
There are tons of articles and videos on the web telling people how to sharpen a knife or a chopper. Some are shown by professional chef. However, none could help a layman sharpening a knife or a chopper properly
Why?
The secret of sharpening a knife is to have the knife always maintaining at a constant angle of about 20 degree to the surface of the sharpening stone or sand paper when sharpening a knife. If the knife edge is irregular, the knife will never be sharp.
How?
To maintain a constant angle, one can use something like a thicker steel ruler to provide a shim or a spacer to “wedge” the knife at about 20 degree angle to the surface of the stone. The trick is on how to stick the ruler to the knife while sharpening the knife.
A Simple Method
a) Find a piece of PVC electrical trunking about the length of the knife. One may be able to get one free from the electricians as they often have some waste piece lying around in the work places; the PVC trunking will usually have a "tongue and groove" arrangement to snap the cover in place;
Wednesday, December 8, 2010
How to Sharpen a Planer Blade
Introduction
There are many ways to sharpen a planer blade instead of replacing and throwing them away. This article will introduce one easy way.
The Planer and Planer Blades
The planer used is as shown. It has 2 blades, each has a length of 3-1/4" and are made of HSS steel.

When the blades are blunt, it will not give a good cutting surface on the wood and the surface will have a fluffy feeling.
 The Sharpening Tools
The Sharpening ToolsThe usual way to sharpen the blade is to use a standard blade sharpening tool which has adjusting screws for angle and other adjustments. Grinding stones are often used. The sharpening work will require some professional skill to prepare grinding stones etc. This article will introduce a simple and yet effective way for DIYs using tools that can be made in just less than ½ hour. No professional skill really required.
The Materials
a) A base made from a piece of plywood measuring around 100 mm x 75 mm ( 4” x 3”) or with the width to suit the length of the blade;
b) A 15 mm PVC tube of about 75 mm (3”) in length;
c) 4 wood screws and washers; 2 shorter ones to tighten the blade to the base and 2 longer ones to tighten to the base to a PVC tube for adjustment of the blade angle;
d) 2 pieces of water base sand papers; one of 240 grade and the other of 300 grade or finer
e) Optional: a set of rollers to be mounted underneath the 15 mm PVC tube so that the base can slide freely on the sand papers. One can use the small rollers that is stripped from the spoilt computer mouse for this purpose.
Other tools required are electric drills and suitable drill bits
The Set Up
a) Drill 2 rows of holes and 2 small holes as shown on the base
b) Drill 2 small holes on the PVC tube to hold the longer screws

The Completed Assembly

Note:
1. One can omit having rollers mounting beneath the PVC if one can always place the PVC tube outside the sand paper area. Anyway, PVC tube are replaceable if they are worn.
2. Constantly check the grinding surface of the blade and adjust the angle of the blade to be grinded. When the angle is correct, make a marking on the PVC tube and the base.
3. When the blade is ready, one should feel the blurs on the opposite edge of the blade. Dismantle the blade and grind away the blur on a fine sand paper. To ensure the blade is always placed at a small angle to the sand paper, one can use a steel ruler or the back of another sand paper to "jack" up the opposite end of the blade when grinding away the blurs.
Thursday, October 7, 2010
Access Denied in Windows 7 Registry
Windows 7 is fast and easy to use but many users said they had tried and went back to XP. They said Windows 7 was not stable. Some complained about program not able to run or run slower than XP after some usages. Reinstallation of these programs often failed. This article will describe a way to solve some of these problems.
Why?
One of the problems is the denial of access to change certain keys required by the programs in the Registry. After some period, the ownership or the permission of the Registry key will be changed for some reasons, probably caused by User Account Control (UAC). The programs will lose the privilege to access and change these keys under normal operation. The solution is to restore the ownership and permission of these keys.
How ?
a) Prepare to check which key was denied the access.
To monitor the Registry, download Process Monitor . Install and run.
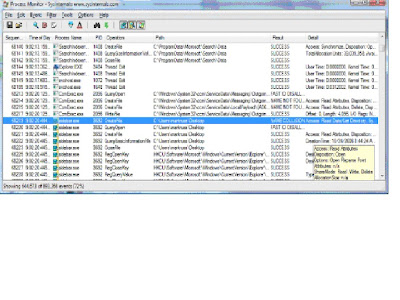 3. To limit the number of events to be display, in the “Filter” menu, select “Filter”
3. To limit the number of events to be display, in the “Filter” menu, select “Filter” 4. In the Architecture dropdown box, select “Result” and type in “ACCESS DENIED” in the box as shown
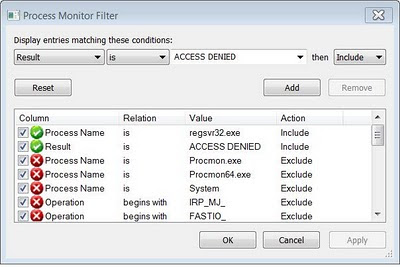
5. Click ok. The monitor is now ready to capture any access denial events for study.
b) Run the faulty application or installation or any program again. this time, check if there are Registry keys being denied access. Note down this key and use “Regedit” to reclaim ownership or permission to change these keys.
What if there are plenty of Registry to Change?
When there is a lot of keys to reclaim ownership or permission, it may be necessary to reset the entire Registry to the defaulted ownership or permission.
How ?
Important Notes: It is advisable to backup by exporting the entire Registry or otherwise save in another disk or partition. The reset of ownership or permission by SubInACL can upset some programs.
1. Download SubInACL which is a program that will enable administrators to manage files, registry keys, and services.
2. Unzip and run SubInACL. It will create a new folder called “Windows Resource Kits/Tools” inside the Program Files (x86) folder.
3. Start up “NotePad”. Copy and paste the following
subinacl /subkeyreg HKEY_LOCAL_MACHINE /grant=administrators=f
subinacl /subkeyreg HKEY_CURRENT_USER /grant=administrators=f
subinacl /subkeyreg HKEY_CLASSES_ROOT /grant=administrators=f
subinacl /subdirectories %SystemDrive% /grant=administrators=f
subinacl /subkeyreg HKEY_LOCAL_MACHINE /grant=system=f
subinacl /subkeyreg HKEY_CURRENT_USER /grant=system=f
subinacl /subkeyreg HKEY_CLASSES_ROOT /grant=system=f
subinacl /subdirectories %SystemDrive% /grant=system=f
4. Save NotePad file as “Reset.cmd” in the “Windows Resource Kits/tools” folder.
5. In the box of the Windows Startup Button, enter “cmd” (without quotes) and rightclick “cmd.exe” when the file appears at the top of the window and select to run as Administor.
6. Type “cd C:\Program Files (x86)\Windows Resource Kits\Tools” at the prompt, follow by “reset.cmd”
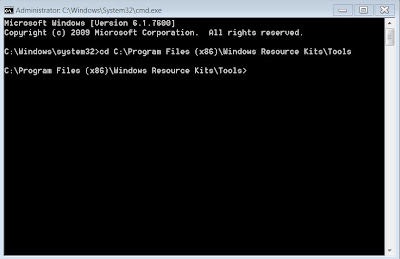
7. The program will run for the next 3 minutes to change all the ownership and permission of the entire keys in the Registry to the default value
Tuesday, August 24, 2010
The Tokyo Tunnel - G-Cans
Introduction
The Tokyo flood tunnels – G-Cans project started construction in 1992 and completed in 2004, about 12 years later. It was just in time to be tested in tyhoon 22 in 2004 when 14 families were reported to be affected instead of 236 families before the completion of the project. The tunnel collects water from Tokyo downtown district and discharge it into the Edogawa river.
The Tunnel
The tunnel is 10m in diameter and about 6.3 kilometers (four miles) long. It is buried 50 metre under the ground in the Tokyo suburbs.
It has 5 concrete silos, each having a diameter of about 32 metres and is about 70 metres tall.
The tunnel is connected to a gigantic water tank measuring about 78m width, 177m long and 25m tall (or 350,000 m3). The tank is propped by 59 numbers of gigantic pillar, each weighing about 500 tons. As the pillars look like those in ancient temples, some named this water tank “the underground temple of Tokyo”.
Connected to this water tank are series of water pump that have a total output of 14,000 hp or 10 MW. They can discharge flood water up to 200 m3 per second or one Olympic pool water in 10 seconds.
The Cost
Estimated to be about US 2.0 billion
The Volume
The tunnel can hold approximately 640,000 m3 of flood water.
Monday, August 23, 2010
Web Query Hangs
Introduction
Users of Microsoft Excel and other web query software, like IMACROS, often query websites to get the web information for stocks or other purposes. These users will write scripts to automate the process. Sometimes, the process will hang causing lost of data. This article will describe methods to overcome this problem.
Why it Hangs?The process will hang either because the website is down or because the web traffic is high. A webpage usually takes 5 to 6 seconds to download may take up to 10 minutes or even hours.
How to Over come?
The following methods have been tried without much success.
a) Introduce timeout events in scripts or VBAThe script is waiting for a webpage to download and will not activate the timeout under such events.
b) Ping the website before proceeding to download
This will only help if the website is down but it will not help when there is a delay due to heavy traffic.
The better method is to modify the window registry’s internet setting with a timeout of appropriate delay. This is because most browsers use this delay in the internet setting.
http://support.microsoft.com/kb/181050
How to Modify the Registry?
The timeout is not native in the registry’s internet setting. It will have to be created under
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings]. The keyword is "ReceiveTimeout”. Its value will depend on normal delay in webpage download.
The Window default is
Internet Explorer 4.0 and Internet Explorer 4.01 --- 5 minutesIn VBA, add the following code before downloading the data
Internet Explorer 5.x and Internet Explorer 6.x---- 60 minutes
Internet Explorer 7 and Internet Explorer 8 ------- 60 minutes
Set myWS = CreateObject("WScript.Shell")'write registry keymyWS.RegWriteThe value of “15000” means a delay of 15 seconds. Insert the same code just after the download script and change the value to suit normal surfing.
"HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet " &
_"Settings\ReceiveTimeout", "15000", "REG_DWORD"
Saturday, August 21, 2010
Error Message for Dynamic Link Library mscvp90.dll
Introduction
When installing Ad-aware program, one will get the following error message for some PCs:
"procedure entry point?_xfunc@tr1@std@@YAXXZ cannot be located in the dynamic link library MSVCP90.dll "
Why?
This error is due to a wrong version of msvcp90.dll being installed by some programs for some reasons.
The dll is one of the C Run-Time Libraries for Visual C++ and programs such as Ad-aware use them.
According to some descriptions, there are 2 versions of such dll having the same name, msvcp90.dll, one for 64 bits and the other for 32 bits machine. XP operating system is a 32 bit machine.
What Next?If one is using a XP operating system and has encountered the problem.
Step 1: Download the correct version of Microsoft Visual C++ 2008 Redistributable Package (x86) from the following website for XP machines
http://www.microsoft.com/downloads/en/confirmation.aspx?familyId=9b2da534-3e03-4391-8a4d-074b9f2bc1bf&displayLang=en
Step 2 : Locate the directory C:\WINDOWS\WinSxS\x86_Microsoft.VC90.CRTxxxxx. In the directory, one should find 3 Nos of 90.dll files. Rename these files with an extension of .tmp. If one has 2 directories of similar name, do the same.
Step 3: Run the downloaded installation program called “credist_x86.exe”. The installation program will automatically uninstall and reinstall the correct version of 90.dll programs.
Step 4: Locate the directory C:\WINDOWS\WinSxS\x86_Microsoft.VC90.CRTxxxxx again. One will find the new 90.dll programs. Copy all the 3 programs to “c:\windows\system32”
Friday, August 20, 2010
Marina Barrage - Fighting With Nature
There was recent spate of flooding in Singapore. The famous Orchard Road was under 300 mm of water. Some blamed the Marina Barrage that was completed 3 years ago. This article will examine how the barrage works and if it can alleviate flooding in low-lying areas.
The Marina Barrage
The Marina Barrage (Chinese:滨海堤坝) is a 350 metres low level dam in Singapore built across the mouth of the bay, between Marina East and Marina South. It was officially opened on 1 November 2008.
The barrage serves 3 purposes:-
a) Provide Water Supply
b) Perform Flood Control
c) Lifestyle Attraction
The video about the barrage can be found here
How the Barrage Works?
During heavy rain, the series of 9 crest gates at the dam will be opened to release flood water into the open sea when the tide is low. The 7 Nos of 40 m3/s (about 2.5 MW @ 3.5 m head) pumps, capable of pumping an Olympics-size swimming pool per minute will work when the tide is high. This mechanism is supposed to alleviate flooding in the low-lying areas in the city such as Chinatown, Boat Quay, Jalan Besar and Geylang.
The video of the crest gate and the pumps can be found here and here.
The Marina Basin
 The Marina Basin has a surface area of about 240 ha (240,000 m2). It is linked to a 100-km2 rain catchment area shown green in the attached model. During raining days, the drains and canals will channel the flood water into the Marina Basin.
The Marina Basin has a surface area of about 240 ha (240,000 m2). It is linked to a 100-km2 rain catchment area shown green in the attached model. During raining days, the drains and canals will channel the flood water into the Marina Basin.The flood
A series of flood occurring after the Barrage was completed

Can the Marina Barrage Cope?
The Barrage and the basin will not eliminate flooding totally if there is a very heavy downpour and the tide is high. This is because the rain fall from the water catchment, if more than those on 17 July, may raise the water level Marina Basin by more than 4.0 metres (discounting the retained water on the surface of the catchment and the buffer in drains/canals/river) during a heavy downpour as shown in table 1.

What Can We Do?
a) Reduce the Water Catchment Area
If we were to reduce the catchment area by 40%, this will reduce the water level rise in the basin by about the same proportion to 4.5 metres per hour without pumps and 4.0 metres per hour with pumps in full operation. The alternative is to regulate the flood water flow from higher areas.
b) Allow More Buffer Capacity In Basin
With the present barrage, there is a limit on how much a buffer can be created in the basin because the gates are not totally water tight. There will be seawater leeching into the basin if there is large difference in the level of water in the basin and the open sea; also, the pumping electricity cost would be high if we keep the water level in the basin low.
Reducing the water catchment area appears to be a better of the 2 solutions for the present setup at the Marina Barrage.
Sunday, July 25, 2010
Where Long Term Funds Park Their Money
The Investment Company Institution (ICI) keeps in touch with the Fund Managers (The Funds), their shareholders, directors and investment advisers regularly. They aim to facilitate the effective functioning of Funds under the U.S. legislative and regulatory framework. They keep and release the Funds' investment in local as well as in foreign countries. This article will aim to introduce ICI as well as to analyse the data they have collected for the information of the readers.
The Data Collections
The data collected by ICI can be found here in this PDF file.
The data tabulated out how much the Funds have invested in Foreign and Domestic equities as well as in bonds and other investment vehicles.
Graphical Plot
The following is a graphical plot of the data kept by ICI for Foreign and domestic equities.

(Doubleclick to enlarge)
Divergence Between Equities and Funds
There is a divergence between DOW and the US domestic funds as shown in the following graph. This graph illustrates that the US domestic equity Funds decreases as DOW increases in value during the period between March 2009 and April 2010. The LTF withdrew even more funds from the domestic equity market during period between April 2010 to present date.
Thursday, July 1, 2010
Keeping Virus Away The Easy Way
Computer viruses often attack the Registry of the XP operating system, making computer going hire-wired; sometimes, it immobilizes the computer and make them hanged. Often, users just have to re-install a new copy of the XP operation system but one will have to re-install all the programs and all other stuffs in the computer. This article tells how one can restore the computer to its original condition when such viruses attacked.
What is Registry and How Viruses Can attack it?
Registry is a place where XP keeps all the information about the computer's hardware and software. It is being used by all the users including 3rd party hardware and software to find where data are stored in the harddisk. If a new program has just been installed or files added, it will update its record. Registy is the one place where it is most vulnerable to virus attacks. Once the viruses reside in the registry, they can be loaded into the computer memory. It will then take over the computer's operation. Sometimes, using normal methods just cannot get rid of these viruses.
What can we do to prevent virus attacks?
We can install virus protection software, firewalls, virus scanning software etc; however, this will never be able to keep all the viruses away. Some viruses have learning capabilities and may lock themselves such that it will prevent users or any virus software from detecting and deleting them.
However, we can do the following to prevent these viruses from attacking the computer:-
a) Regular maintenance. Scanning, detecting, preventing and deleting the existence of viruses using one or more of the following programs
1) Virus Shield, such as norton, trendmircro, Macfee shields etc
2) Spyware and Malware Scanner, such as Adaware
3) Hijackthis
Run these program once everyday or every other day. On detection of the viruses, scan the computer in full using Virus full scanning programs
b) Regularly saving a copy of the registry, booting files and other information so that one can restore them. There are a few alternatives
1. Registry Saving and Restoration
XP can save a copy of the registry automatically whenever there is a change in the registry such as after each installation of a new program. These registry files are installed in the "System Volume Information" folder.
When there is need to restore the registry or when virus attack the computer, one can restore the registry to the saved position. For instruction. follow this link.
Alternatively, one can save a copy of the registry manually by using the "export" function of the Registry Editor. To access the Registry Editor, click Start button and then in the dropdown box, enter "Regedit" (without quotes) and click ok.
2) Backup a copy of System State
This will save not only a copy of the Registry but also the booting files and the COM+ files. The complete system state for the restoration of the XP system. One would need a free disk space of about 600 MB.
2. Click Start, then in the All program/Accessories/System Tool folder, select the Backup program and finally, reaching the following screen.
Select "Let me choose what to backup" and click Next. Now, expand My Computer folder and then select to put a tick in the "System state" folder as shown and click Next
Choose a place to store the backup files using Browse button and then enter a name for this backup file. It is good to store the backup file in a thumbdrive or RW CD or another harddisk so that it can be read and the backup file restored in case of harddisk failures. Note that the backup file can be more than 500 MB
Click Next
Select Advance button and Normal in dropdown box of the subsequent screens, one would reach the following screen to select the verification of file after backup. Tick the box and then Next. The computer will do the rest of job.
Step 2: Restoring the backup files
1. After having installed a new XP operating system in the existing harddisk and provided one has not erase or change any program or file, one can restore the XP system to its orginal condition
2. Following Step 1-2, then choose restore files and settings instead, one should reach the following screen. Browse to the directory of the backup file and doubleclick it, a new screen should show the folder "System State". Tick the box to select and click Next. Click advance in the next screen. Change the default setting if necessary.
NOTE: The backup program, NTBACKUP, is not installed by default in Windows XP Home Edition. Install it using the instructions available at: Q302894.
Select the System State check box
NOTE: If you want to back up your system settings as well as your data files, you should back up all the data on your computer plus the System State data, which includes such things as the registry, the COM+ class registration database, files under Windows File Protection, and boot files.
In the Backup destination list, click the backup destination that you want to use.
If you clicked File in the previous step, type the full path and file name that you want in the Backup media or file name box. Note that you can also specify a network share as a destination for the backup file. Click Start Backup . The Backup Job Information dialog box appears. Under If the media already contains backups, use one of the following steps:
If you want to append this backup to previous backups, click Append this backup to the media.
If you want to overwrite previous backups with this backup, click Replace the data on the media with this backup .
Click Advanced. Select the Verify data after backup check box.
In the Backup Type box, click the type of backup that you want. When you click a backup type, a description of that backup type is displayed under "Description." Click OK , and then click Start Backup . A Backup Progress dialog box appears, and the backup starts. When the backup is complete, click Close.
Important Note:
Viruses sometimes reside in the Registry and also the booting files. It is important to make sure that when one save a copy of the Registry or booting files, one does not save also the viruses. To make sure
a) Clean the computer before saving;
b) Always save new copies in different names;
Enabling DVI Interface in LCD Monitor
- Enter Device Manager by clicking Start button, then select run, in the dropdown box, enter "devmgmt.msc" (without quotes) and click ok.
- In the Monitors folder, one should find some monitor drivers and a driver called "Plug and Play Monitor". Remove all the monitor drivers, left except the "Plug and Play Monitor". One can easily remove the drivers by right clicking and then either disable or uninstall the drivers.
- Switch off the monitor and computer. Remove the VGA cable and install or left the DVI cable attached to the monitor.
- Re-start the computer, one should boot up with signal
- Install the DVI software as provided by the manufacturer. Check the Display property to ensure that the DVI software is properly installed.
- doubleclicking the VGA driver and in the "Driver" tab,
- select "Update Driver" and then
- select "No, no this time", click next
- select "install from a list or specific location", click next
- select "Don't search, I will choose the driver to install" click next
- finally, select "Plug and Play monitor" and click next to install .
How To Improve WiFi Reception
There are many ways one can improve the WiFi reception at home. But before one jumps to do any physical changes to WiFi systems, including ...

-
1. How Air-conditioning works? 2. The Special Tools and Equipment? 3. The Professional Must Owned Equipment? 4. The Professionals Verse ...
-
9 April 2018 1) The Hard Wiring Connection 2) Blue Tooth Connection 3) More about SPDIF and HDMI (ARC) 4) Why HDMI (ARC) Not Working Xiao...
-
There are many ways one can improve the WiFi reception at home. But before one jumps to do any physical changes to WiFi systems, including ...






