Introduction Computer viruses often attack the Registry of the XP operating system, making computer going hire-wired; sometimes, it immobilizes the computer and make them hanged. Often, users just have to re-install a new copy of the XP operation system but one will have to re-install all the programs and all other stuffs in the computer. This article tells how one can restore the computer to its original condition when such viruses attacked.
What is Registry and How Viruses Can attack it?Registry is a place where XP keeps all the information about the computer's hardware and software. It is being used by all the users including 3rd party hardware and software to find where data are stored in the harddisk. If a new program has just been installed or files added, it will update its record. Registy is the one place where it is most vulnerable to virus attacks. Once the viruses reside in the registry, they can be loaded into the computer memory. It will then take over the computer's operation. Sometimes, using normal methods just cannot get rid of these viruses.
What can we do to prevent virus attacks?We can install virus protection software, firewalls, virus scanning software etc; however, this will never be able to keep all the viruses away. Some viruses have learning capabilities and may lock themselves such that it will prevent users or any virus software from detecting and deleting them.
However, we can do the following to prevent these viruses from attacking the computer:-
a) Regular maintenance. Scanning, detecting, preventing and deleting the existence of viruses using one or more of the following programs
1) Virus Shield, such as norton, trendmircro, Macfee shields etc
2) Spyware and Malware Scanner, such as Adaware
3) Hijackthis
Run these program once everyday or every other day. On detection of the viruses, scan the computer in full using Virus full scanning programs
b) Regularly saving a copy of the registry, booting files and other information so that one can restore them. There are a few alternatives
1. Registry Saving and Restoration
XP can save a copy of the registry automatically whenever there is a change in the registry such as after each installation of a new program. These registry files are installed in the "System Volume Information" folder.
When there is need to restore the registry or when virus attack the computer, one can restore the registry to the saved position. For instruction. follow this
link.
Alternatively, one can save a copy of the registry manually by using the "export" function of the Registry Editor. To access the Registry Editor, click Start button and then in the dropdown box, enter "Regedit" (without quotes) and click ok.
2) Backup a copy of System State
This will save not only a copy of the Registry but also the booting files and the COM+ files. The complete system state for the restoration of the XP system. One would need a free disk space of about 600 MB.
Step 1: Backing Up
1. Make sure the computer is not infested with viruses by performing all the necessary virus or spyware scans available.
2. Click Start, then in the All program/Accessories/System Tool folder, select the Backup program and finally, reaching the following screen.
Select "Let me choose what to backup" and click Next. Now, expand My Computer folder and then select to put a tick in the "System state" folder as shown and click Next
Choose a place to store the backup files using Browse button and then enter a name for this backup file. It is good to store the backup file in a thumbdrive or RW CD or another harddisk so that it can be read and the backup file restored in case of harddisk failures. Note that the backup file can be more than 500 MB
Click Next
Select Advance button and Normal in dropdown box of the subsequent screens, one would reach the following screen to select the verification of file after backup. Tick the box and then Next. The computer will do the rest of job.
Step 2: Restoring the backup files
1. After having installed a new XP operating system in the existing harddisk and provided one has not erase or change any program or file, one can restore the XP system to its orginal condition
2. Following Step 1-2, then choose restore files and settings instead, one should reach the following screen. Browse to the directory of the backup file and doubleclick it, a new screen should show the folder "System State". Tick the box to select and click Next. Click advance in the next screen. Change the default setting if necessary.
NOTE: The backup program, NTBACKUP, is not installed by default in Windows XP Home Edition. Install it using the instructions available at:
Q302894.
Select the System State check box
NOTE: If you want to back up your system settings as well as your data files, you should back up all the data on your computer plus the System State data, which includes such things as the registry, the COM+ class registration database, files under Windows File Protection, and boot files.
In the Backup destination list, click the backup destination that you want to use.
If you clicked File in the previous step, type the full path and file name that you want in the Backup media or file name box. Note that you can also specify a network share as a destination for the backup file. Click Start Backup . The Backup Job Information dialog box appears. Under If the media already contains backups, use one of the following steps:
If you want to append this backup to previous backups, click Append this backup to the media.
If you want to overwrite previous backups with this backup, click Replace the data on the media with this backup .
Click Advanced. Select the Verify data after backup check box.
In the Backup Type box, click the type of backup that you want. When you click a backup type, a description of that backup type is displayed under "Description." Click OK , and then click Start Backup . A Backup Progress dialog box appears, and the backup starts. When the backup is complete, click Close.
Important Note:
Viruses sometimes reside in the Registry and also the booting files. It is important to make sure that when one save a copy of the Registry or booting files, one does not save also the viruses. To make sure
a) Clean the computer before saving;
b) Always save new copies in different names;
c) Make a copy just after a reinstallation of the XP system
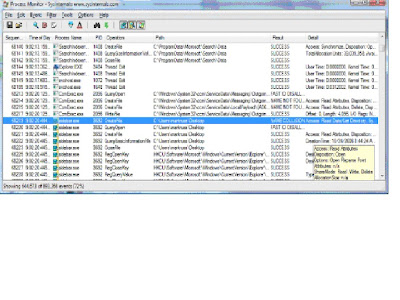 3. To limit the number of events to be display, in the “Filter” menu, select “Filter”
3. To limit the number of events to be display, in the “Filter” menu, select “Filter” 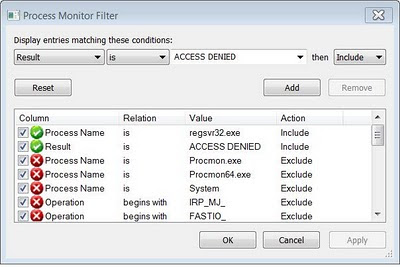
 The Marina Basin has a surface area of about 240 ha (240,000 m2). It is linked to a 100-km2 rain catchment area shown green in the attached model. During raining days, the drains and canals will channel the flood water into the Marina Basin.
The Marina Basin has a surface area of about 240 ha (240,000 m2). It is linked to a 100-km2 rain catchment area shown green in the attached model. During raining days, the drains and canals will channel the flood water into the Marina Basin.









